The best pen tester tools: sniffers and working with packages. Network traffic analyzer sniffer
What is Intercepter-NG
Let's consider the essence of ARP functioning on simple example. Computer A (IP address 10.0.0.1) and Computer B (IP address 10.22.22.2) are connected by an Ethernet network. Computer A wants to send a data packet to computer B; it knows the IP address of computer B. However, the Ethernet network they are connected to does not work with IP addresses. Therefore, in order to transmit via Ethernet, computer A needs to know the address of computer B on the Ethernet network (MAC address in Ethernet terms). The ARP protocol is used for this task. Using this protocol, computer A sends a broadcast request addressed to all computers in the same broadcast domain. The essence of the request: “computer with IP address 10.22.22.2, provide your MAC address to the computer with MAC address (for example, a0:ea:d1:11:f1:01).” The Ethernet network delivers this request to all devices on the same Ethernet segment, including computer B. Computer B responds to computer A to the request and reports its MAC address (eg 00:ea:d1:11:f1:11) Now, Having received the MAC address of computer B, computer A can transmit any data to it via the Ethernet network.
To avoid the need to use the ARP protocol before each data sending, the received MAC addresses and their corresponding IP addresses are recorded in the table for some time. If you need to send data to the same IP, then there is no need to poll devices every time in search of the desired MAC.
As we just saw, ARP includes a request and a response. The MAC address from the response is written to the MAC/IP table. When a response is received, it is not checked in any way for authenticity. Moreover, it doesn't even check whether the request was made. Those. you can immediately send an ARP response to the target devices (even without a request), with spoofed data, and this data will end up in the MAC/IP table and will be used for data transfer. This is the essence of the ARP-spoofing attack, which is sometimes called ARP etching, ARP cache poisoning.
Description of the ARP-spoofing attack
Two computers (nodes) M and N on an Ethernet local network exchange messages. Attacker X, located on the same network, wants to intercept messages between these nodes. Before the ARP-spoofing attack is applied on the network interface of host M, the ARP table contains the IP and MAC address of host N. Also on the network interface of host N, the ARP table contains the IP and MAC address of host M.
During an ARP-spoofing attack, node X (the attacker) sends two ARP responses (without a request) - to node M and node N. The ARP response to node M contains the IP address of N and the MAC address of X. The ARP response to node N contains the IP address M and MAC address X.
Since computers M and N support spontaneous ARP, after receiving an ARP response, they change their ARP tables, and now the ARP table M contains the MAC address X bound to the IP address N, and the ARP table N contains the MAC address X, bound to the IP address M.
Thus, the ARP-spoofing attack is completed, and now all packets (frames) between M and N pass through X. For example, if M wants to send a packet to computer N, then M looks in its ARP table, finds an entry with the host’s IP address N, selects the MAC address from there (and there is already the MAC address of node X) and transmits the packet. The packet arrives at interface X, is analyzed by it, and then forwarded to node N.
Many users computer networks, in general, such a concept as a “sniffer” is unfamiliar. Let’s try to define what a sniffer is, in the simple language of an untrained user. But first, you still have to delve into the predefinition of the term itself.
Sniffer: what is a sniffer from the point of view of the English language and computer technology?
In fact, it is not at all difficult to determine the essence of such a software or hardware-software complex if you simply translate the term.
This name comes from the English word sniff (sniff). Hence the meaning of the Russian term “sniffer”. What is a sniffer in our understanding? A “sniffer” capable of monitoring the use of network traffic, or, more simply put, a spy who can interfere with the operation of local or Internet-based networks, extracting the information he needs based on access through TCP/IP data transfer protocols.
Traffic analyzer: how does it work?
Let’s make a reservation right away: a sniffer, be it a software or shareware component, is capable of analyzing and intercepting traffic (transmitted and received data) exclusively through network cards (Ethernet). What happens?
The network interface is not always protected by a firewall (again, software or hardware), and therefore interception of transmitted or received data becomes just a matter of technology.

Within the network, information is transmitted across segments. Within one segment, data packets are supposed to be sent to absolutely all devices connected to the network. Segmented information is forwarded to routers (routers), and then to switches (switches) and concentrators (hubs). Sending information is done by splitting packets so that the end user receives all parts of the package connected together from completely different routes. Thus, “listening” to all potential routes from one subscriber to another or the interaction of an Internet resource with a user can provide not only access to unencrypted information, but also to some secret keys, which can also be sent in such an interaction process. And here the network interface turns out to be completely unprotected, because a third party intervenes.
Good intentions and malicious purposes?
Sniffers can be used for both good and bad. Not to mention the negative impact, it is worth noting that such software and hardware systems are used quite often system administrators, which try to track the actions of users not only on the Internet, but also their behavior on the Internet in terms of visited resources, activated downloads to computers or sending from them.

The method by which the network analyzer works is quite simple. The sniffer detects outgoing and incoming traffic of the machine. In this case, we are not talking about internal or external IP. The most important criterion is the so-called MAC address, unique for any device connected to global web. It is used to identify each machine on the network.
Types of sniffers
But by type they can be divided into several main ones:
- hardware;
- software;
- hardware and software;
- online applets.
Behavioral detection of the presence of a sniffer on the network
You can detect the same WiFi sniffer by the load on the network. If it is clear that the data transfer or connection is not at the level stated by the provider (or the router allows), you should pay attention to this immediately.

On the other hand, the provider can also run a software sniffer to monitor traffic without the user's knowledge. But, as a rule, the user does not even know about it. But the organization providing communication and Internet connection services thus guarantees the user complete security in terms of intercepting floods, self-installing clients of various Trojans, spies, etc. But such tools are rather software and do not have much impact on the network or user terminals.
Online resources
But an online traffic analyzer can be especially dangerous. A primitive computer hacking system is built on the use of sniffers. The technology in its simplest form boils down to the fact that an attacker initially registers on a certain resource, then uploads a picture to the site. After confirming the download, a link to an online sniffer is issued, which is sent to the potential victim, for example, in the form email or the same SMS message with a text like “You received a congratulation from so-and-so. To open the picture (postcard), click on the link.”

Naive users click on the specified hyperlink, as a result of which recognition is activated and the external IP address is transferred to the attacker. If he has the appropriate application, he will be able not only to view all the data stored on the computer, but also to easily change the system settings from the outside, about which local user won’t even guess, mistaking such a change for the impact of a virus. But the scanner will show zero threats when checking.
How to protect yourself from data interception?
Whether it's a WiFi sniffer or any other analyzer, there are still systems to protect against unauthorized traffic scanning. There is only one condition: they need to be installed only if you are completely confident in “wiretapping”.

Such software most often called “antisniffers”. But if you think about it, these are the same sniffers that analyze traffic, but block other programs trying to receive
Hence the legitimate question: is it worth installing such software? Perhaps its hacking by hackers will cause even more harm, or will it itself block what should work?
In the very simple case With Windows systems, it is better to use a built-in firewall as protection. Sometimes there may be conflicts with installed antivirus, but this often only applies to free packages. Professional purchased or monthly activated versions do not have such shortcomings.
Instead of an afterword
That's all about the concept of “sniffer”. I think many people have already figured out what a sniffer is. Finally, the question remains: how correctly will the average user use such things? Otherwise, among young users you can sometimes notice a tendency towards computer hooliganism. They think that hacking someone else's computer is something like an interesting competition or self-affirmation. Unfortunately, none of them even think about the consequences, but it is very easy to identify an attacker using the same online sniffer by his external IP, for example, on the WhoIs website. True, the location of the provider will be indicated as the location, however, the country and city will be determined exactly. Well, then it’s a matter of little things: either a call to the provider to block the terminal from which unauthorized access was made, or a criminal case. Draw your own conclusions.
At installed program Determining the location of the terminal from which an access attempt is being made is even simpler. But the consequences can be catastrophic, because not all users use those anonymizers or virtual proxy servers and don’t even have a clue about the Internet. It would be worth learning...
Interceptor is a multifunctional network tool that allows you to obtain data from traffic (passwords, instant messenger messages, correspondence, etc.) and implement various MiTM attacks.
Intercepter program interface
Main functionality
- Interception of instant messenger messages.
- Interception of cookies and passwords.
- Interception of activity (pages, files, data).
- Ability to spoof file downloads by adding malicious files. Can be used in conjunction with other utilities.
- Replacing Https certificates with Http.
Messengers Mode– allows you to check correspondence that was sent in unencrypted form. It was used to intercept messages in such instant messengers as ICQ, AIM, JABBER messages.
Ressurection Mode– recovery of useful data from traffic, from protocols that transmit traffic in clear text. When the victim views files, pages, data, they can be partially or completely intercepted. Additionally, you can specify the size of the files so as not to download the program in small parts. This information can be used for analysis.
Password Mode– mode for working with cookies. In this way, it is possible to gain access to the victim's visited files.
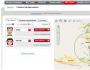
Scan mode– main mode for testing. To start scanning, click right click mice Smart Scan. After scanning, all network participants will be displayed in the window, their operating system and other parameters.
Additionally, in this mode you can scan ports. You must use the Scan Ports function. Of course, there are much more functional utilities for this, but the presence of this function is an important point.
If we are interested in a targeted attack on the network, then after scanning we need to add the target IP to Nat using the command (Add to Nat). In another window it will be possible to carry out other attacks.
Nat Mode. The main mode, which allows you to carry out a number of attacks via ARP. This is the main window that allows targeted attacks.
DHCP mode. This is a mode that allows you to raise your DHCP server to implement DHCP attacks in the middle.
Some types of attacks that can be carried out
Site spoofing
To spoof the victim’s website, you need to go to Target, after which you need to specify the site and its substitution. This way you can replace quite a lot of sites. It all depends on how high-quality the fake is.
Site spoofing
Example for VK.com
Selecting MiTM attack
Changing the injection rule
As a result, the victim opens a fake website when requesting vk.com. And in password mode there should be the victim’s login and password:
To carry out a targeted attack, you need to select a victim from the list and add it to the target. This can be done using the right mouse button.
Adding MiTm attacks
Now you can use Ressurection Mode to recover various data from traffic.
Victim files and information via MiTm attack
Traffic spoofing
Specifying Settings
After this, the victim’s request will change from “trust” to “loser”.
Additionally, you can kill cookies so that the victim logs out of all accounts and logs in again. This will allow you to intercept logins and passwords.
Destroying cookies
How to see a potential sniffer on the network using Intercepter?
Using the Promisc Detection option, you can detect a device that is scanning on the local network. After scanning, the status column will show “Sniffer”. This is the first way to detect scanning on a local network.
Sniffer Detection
SDR HackRF Device
SDR is a kind of radio receiver that allows you to work with different radio frequency parameters. Thus, it is possible to intercept the signal of Wi-Fi, GSM, LTE, etc.
HackRF is a full SDR device for $300. The author of the project, Michael Ossman, is developing successful devices in this direction. The Ubertooth Bluetooth sniffer was previously developed and successfully implemented. HackRF is a successful project that has raised more than 600 thousand on Kickstarter. 500 of these devices have already been sold for beta testing.
HackRF operates in the frequency range from 30 MHz to 6 GHz. The sampling frequency is 20 MHz, which allows you to intercept signals from Wi-FI and LTE networks.
How to protect yourself at the local level?
First, let's use SoftPerfect WiFi Guard software. There is a portable version that takes no more than 4 MB. It allows you to scan your network and display what devices are displayed on it. It has settings that allow you to choose network card and the maximum number of scanned devices. Additionally, you can set the scanning interval.
Ability to add comments for users
Conclusion
Thus, we have considered in practice how to use software to intercept data within the network. We looked at several specific attacks that allow you to obtain login data, as well as other information. Additionally, we looked at SoftPerfect WiFi Guard, which allows you to protect at a primitive level local network from listening to traffic.
SmartSniff allows you to intercept network traffic and display its contents in ASCII. The program captures packets passing through network adapter and displays the contents of packets in text form (protocols http, pop3, smtp, ftp) and in the form of a hexadecimal dump. To capture TCP/IP packets, SmartSniff uses the following techniques: raw sockets - RAW Sockets, WinCap Capture Driver and Microsoft Network Monitor Driver. The program supports the Russian language and is easy to use.
Sniffer program for capturing packets
 |
SmartSniff displays the following information: protocol name, local and remote address, local and remote port, local node, service name, data volume, total size, capture time and last packet time, duration, local and remote MAC address, countries and data packet contents. The program has flexible settings, it implements the function of a capture filter, unpacking http responses, converting IP addresses, the utility is minimized to the system tray. SmartSniff generates a report on packet flows in the form HTML pages. The program can export TCP/IP streams.


The Wi-Fi network packet sniffer module can be used on both normal and monitor modes, but it also supports a third option, the extended mode, for capturing the Wi-Fi network traffic generated by your equipment.
The extended mode allows you to use the while your wireless card is connected to a Wi-Fi network. Apart from viewing signaling packets (beacons, probe requests, probe responses, data packets, etc.), you will be able to view all the TCP, UDP, or Wi-Fi broadcast traffic generated by your system while connected. This way, you will be able to view and analyze all the web browsing ( HTTP) traffic, or any other network connection sent by the Wi-Fi network you are connected to.
This capture mode does not allow you to view Wi-Fi traffic from other channels, since your wireless card is working at a fixed frequency.
The Wi-Fi network sniffer on extended mode and the network packet capture mode sectors are long-awaited new features on Acrylic Wi-Fi Professional v2.3, which is expected to be launched within the next few days.
Download Wireless Network Sniffer for Windows 7/8/8.1/10
If you do not need to view Wi-Fi network packets or use a Wi-Fi network traffic sniffer, download , a free Wi-Fi network and channel sniffer for Windows that allows you to view all the wireless networks within reach. This version supports normal capture and monitor modes.
If you need complete wireless network behavior information, Wi-Fi network sniffer is the right solution for you, since it supports all three Wi-Fi network capture modes, providing Wi-Fi network packet information in real time. A very useful tool for improving wireless network performance, detecting incidents, and learning more about Wi-Fi networking. Try it for free!
And for advanced users, the Acrylic Wi-Fi driver allows you to.